Hello I have an nice phone
ULEFONE Power Armor 13
Good specs etc
Recovery:
-
boot menu: hold power and vol up. when phone vibrates to boot up relaes power and keep holding vol up (caused by the pu button being held constant during bootup)
- in this mode fastboot lets you flash with adb
- recover boots recovery image
- normal is normal boot
-
to boot right into recovery
- hole power off and volume down release pwoer to stop reboot
- once you see logo you can release vol down and it will enter recovery boot
Recently iv had some problems with it and the os has been corupted. I blame spyware
I am about to recover my photos off of this device and then root it with a stock ish android
Im a noob at android development/hacking so would like to document my learning joruny for you
First install adb Getting ADB (Android Debug Bridge) working on linux can be a bit harder than on other operating systems. This guide aims to help with that.
Installation
https://gist.githubusercontent.com/isti03/4104cc33dbf5b741add2a27c8d3a41df/raw/3e7e21bcd0108188628a035f7c8f4fdf447d3f04/adb-linux.md https://forum.xda-developers.com/t/guide-linux-installing-adb-and-fastboot-on-linux-device-detection-drivers.3478678/
1. Install the adb package
Just use your package manager
sudo apt install adb
sudo apt-get install android-tools-adb android-tools-fastboot
https://spmdttool.com/sp-mdt-v3-1904-00
https://spflashtools.com/linux/sp-flash-tool-v6-2124-for-linux
2. Add yourself to the plugdev group
sudo groupadd plugdev
sudo usermod -a -G plugdev $USER
Then reboot
3. Enable Usb debugging on your device
See https://www.getdroidtips.com/enable-usb-debugging/
4. Connect to your device
- Unlock your device
- Run the command
adb devices - Authorize access on a pop-up on your device
- Re-run
adb devices. You should see your device id, anddevicenext to it. - If you get an error,
no permissions (user in plugdev group; are your udev rules wrong?), install theandroid-udevpackage and reboot.
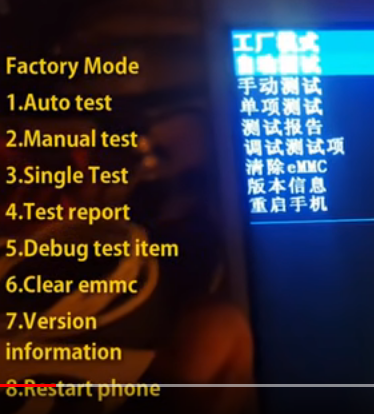
to enter chineis menu hold power and vol down when you see the screen relaeas volum down and then power
Fastboot
fastboot devices ; # ensure we are conected
fastboot getvar all ; # dump bootvars
1544 cd S7S68B7.GQU.Ulefone.HB.HJ.VKPMXY8AE.20220413.V3.03/
1545 ls
1546 fastboot flash super super.img
1547 fastboot getvar all
1548 ls
1549 fastboot reboot
1550 ls
1551 fastboot boot
1552 fastboot reboot
1553 fastboot devices
1554 ls
1555 fastboot flash recovery ../boot_TWRP_220321_magisk_v24300.img
1556 fastboot flash boot boot.img
1557 fastboot flash logo logo-verified.bin
1558 fastboot flash cam_vpu1 cam_vpu1-verified.img
1559 fastboot flash cam_vpu2 cam_vpu2-verified.img
1560 fastboot flash cam_vpu3 cam_vpu3-verified.img
1561 fastboot flash dtbo dtbo-verified.img
1562 fastboot flash gz gz-verified.img
1563 fastboot flash lk lk-verified.img
1564 fastboot flash md1img md1img-verified.img
1565 fastboot flash scp scp-verified.img
1566 fastboot flash spmfw spmfw-verified.img
1567 fastboot flash sspm sspm-verified.img
1568 fastboot flash tee tee-verified.img
1569 fastboot flash vbmeta vbmeta.img
1570 fastboot flash vbmeta_system vbmeta_system.img
1571 fastboot flash vbmeta_vendor vbmeta_vendor.img
1572 fastboot flash userdata userdata.img
1573 fastboot flash super super.img
1574 fastboot reboot